WordPress Security Best Practices: Safeguarding Your Website
This article highlights essential security practices for protecting WordPress sites from various threats, such as brute force attacks, SQL injection, and XSS. By following recommendations for regular updates, using security plugins, and educating users, site owners can significantly reduce risks and ensure the safety of their data.

Here are the main types of attacks that WordPress site owners may encounter:
- Brute Force Attacks
Automated scripts attempt to guess usernames and passwords to gain access to the admin panel. This attack is effective when weak passwords are used. - SQL Injection
Malicious code is injected into database queries through vulnerable forms or URL parameters. This can allow an attacker to access confidential information, alter data, or take control of the site. - Cross-Site Scripting (XSS)
Attackers inject malicious scripts into the site’s pages, which can execute actions on behalf of the user, collect data, or redirect to malicious sites. XSS attacks often exploit vulnerable forms or comments. - DDoS Attacks (Distributed Denial of Service)
The site receives a massive number of requests from various IP addresses, leading to server overload and making it inaccessible to users. - Cross-Site Request Forgery (CSRF)
This attack tricks a user into performing unwanted actions on a site where they are already authenticated. This can result in changing settings or executing operations on behalf of the user without their knowledge. - Logging and Credential Theft
Attackers can intercept user credentials through compromised plugins, themes, or malware installed on the administrator’s computer. - Vulnerabilities in Plugins and Themes
Many plugins and themes contain vulnerabilities that can be exploited for attacks, such as uploading malicious files, executing arbitrary code, or gaining access to confidential information. - Malicious File Uploads
Malicious files uploaded through forms on the site can be used to perform attacks or compromise the server. - XML-RPC Attacks
The XML-RPC interface in WordPress allows various actions to be performed remotely. Attackers can use it for brute force attacks or server overload. - Directory Traversal (Directory Path Attack)
This attack allows access to files and directories outside the site’s web directory, which can lead to the leakage of confidential data. - Remote File Inclusion (RFI) and Local File Inclusion (LFI)
An attacker can include remote or local files to execute arbitrary code on the server. - Phishing via Hacked Sites
Hacked WordPress sites can be used to host phishing pages that trick users into entering their credentials or other confidential information. - Backdoor Attacks
An attacker injects malicious code or creates a “backdoor” on the site, allowing access and bypassing standard authentication procedures. - Supply Chain Attacks
These occur when third-party libraries or plugins are used that may contain malicious code, potentially introducing malware to the site. - Clickjacking
An attack where an attacker uses invisible layers or iframes to trick the user into clicking on hidden elements.
Now that we are aware of all the possible types of attacks on our website, let’s consider how we can protect our site from these threats. Here are some effective strategies to enhance your website’s security:
Protection Against Brute Force Attacks
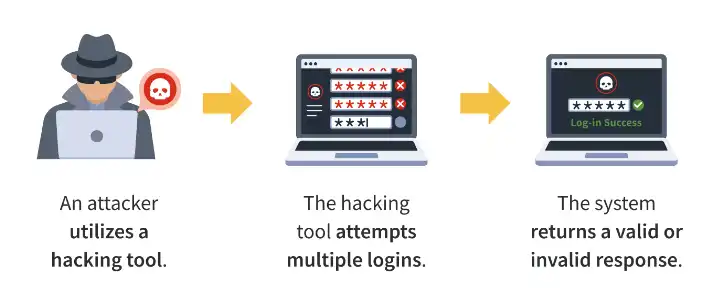
- Security Plugins: Use security plugins like Wordfence, iThemes Security, or Shield Security. I use Wordfence because it offers a comprehensive solution for many types of attacks with very flexible settings. (This is not an advertisement; I haven’t received any money for this.)
- Implement Cloudflare on Your Domain: When Cloudflare detects a brute force attack, it throttles request rates from a single IP address and applies challenge pages like CAPTCHA to ensure that the requests are made by humans. If necessary, suspicious IP addresses are blocked, and the Web Application Firewall filters traffic, protecting login pages. These measures help prevent password guessing and secure the site from being hacked.
- Change the Login URL: There are several plugins available in the official plugin repository that can help you easily change the login page URL.
- Enable Two-Factor Authentication: Implementing two-factor authentication adds a layer of security.
- Limit Login Attempts: This can also be managed with Wordfence, which allows you to restrict the number of login attempts.
- Use Strong Passwords: Always use complex passwords that are generated by WordPress
- Use Salt in Your Config: Utilize the salt generated automatically by visiting the following URL: https://api.wordpress.org/secret-key/1.1/salt/. This salt should be added to your configuration file, making it more difficult to crack passwords if they are generated by WordPress.
Protection Against SQL Injections
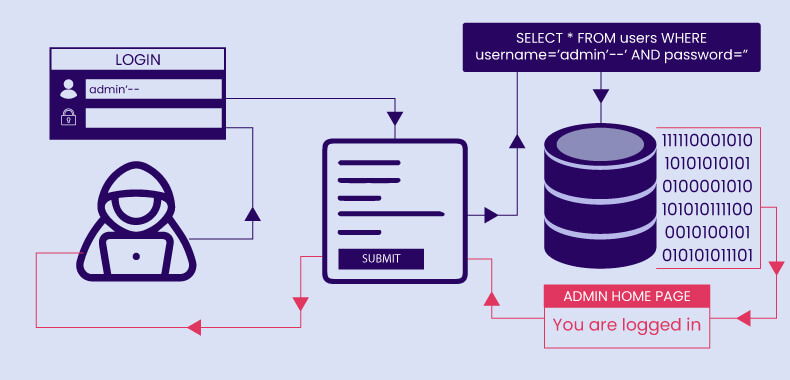
These rules are more applicable to developers than to users:
- Code Standards Compliance: Ensure that your theme or plugin code passes WPCS (WordPress Coding Standards). This guarantees that all variables used in form processing or site queries are properly sanitized.
- Use
$wpdb->prepare(): For custom database queries, utilize $wpdb->prepare( “foo = %s”, ‘a’ );. This helps prevent SQL injection by properly escaping input. - Form Validation: Implement validation not only on the front end but also on the back end. A good developer never trusts client-side data and always verifies it on the server side. Always use functions like sanitize_text_field() or esc_sql().
- Regular Updates: Regularly update WordPress, installed plugins, and themes. This helps eliminate vulnerabilities that could be exploited for SQL injections.
- Use a Web Application Firewall (WAF): Consider using WAFs like iThemes Security, Cloudflare, or Wordfence to add an extra layer of protection against SQL injection attacks.
Protection Against Cross-Site Scripting (XSS)
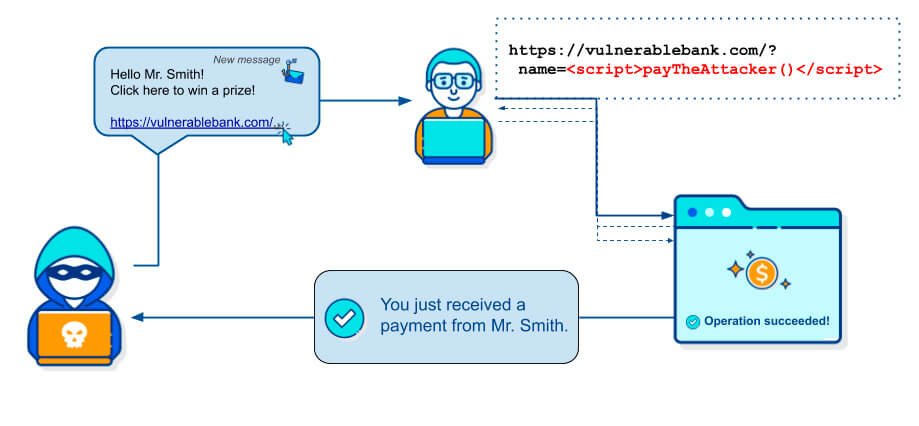
- Install Security Plugins: Use security plugins like Wordfence, iThemes Security, or Shield Security to protect your site.
- Disable HTML Insertion in Comments and Forms: Prevent users from inserting HTML in comments, forms, or other input fields. This can be achieved using filters or built-in WordPress options.
- Regular Updates: Regularly update all components of your site, including plugins, themes, and WordPress itself, to eliminate vulnerabilities that could be exploited for XSS attacks.
- Sanitize and Escape Data: Always sanitize and escape user inputs before outputting them on pages. In WordPress, you can use functions like esc_html(), esc_attr(), and esc_url() to prevent the execution of malicious code.
- Use WordPress Validation Functions: Utilize built-in WordPress functions for validating and filtering data, such as sanitize_text_field(), wp_kses(), and others. This ensures that the data is safe for use.
- Implement Content Security Policy (CSP): Configure Content Security Policy headers to restrict JavaScript execution to trusted sources only. This helps prevent the injection of malicious scripts.
Protection Against DDoS Attacks (Distributed Denial of Service)
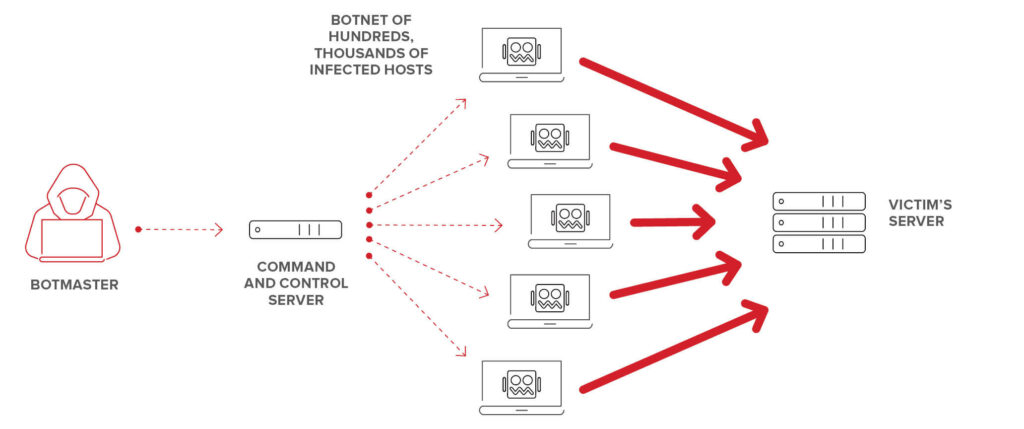
- Install Security Plugins: Use security plugins like Wordfence, iThemes Security, or Shield Security to enhance your site’s protection.
- Implement Cloudflare on Your Domain: Set up Cloudflare for your domain to benefit from its DDoS protection features.
- Install Fail2Ban (F2B) on Your Server: Use Fail2Ban to monitor logs and block IP addresses that show malicious activity, adding an extra layer of security.
- Limit Request Rates: Configure limits on the number of requests from a single IP address over a specified period. This helps prevent server overload during DDoS attacks.
Protection Against Cross-Site Request Forgery (CSRF)
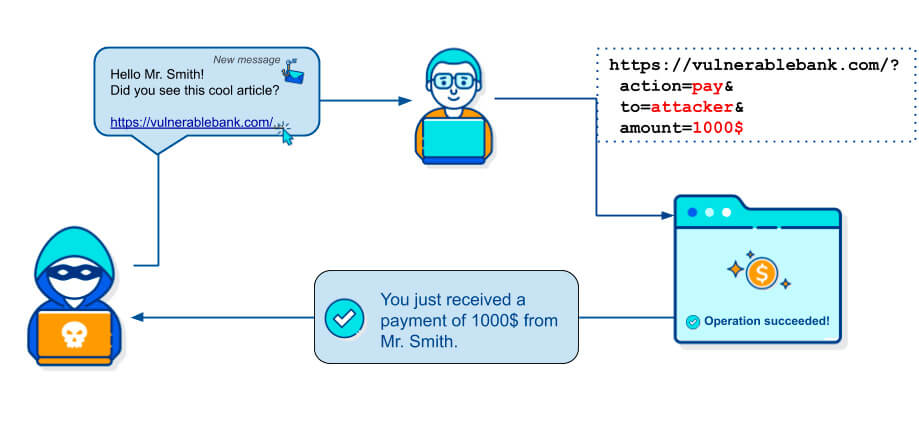
- Regular Updates: Regularly update all components of your site, including WordPress, plugins, and themes, to eliminate vulnerabilities that could be exploited for CSRF attacks.
- Use Security Plugins: Consider installing security plugins that provide additional protection against CSRF attacks, such as Wordfence or iThemes Security.
- Implement CSRF Tokens: Integrate unique tokens into forms and requests that must be validated on the server. WordPress automatically generates tokens using functions like wp_nonce_field() and
check_admin_referer() to ensure that requests originate from authorized users. - Session Isolation: Configure session and cookie settings to restrict access to critical functions only for authenticated users. Use the SameSite attribute to protect cookies.
- Use POST Methods: For actions that can change the server’s state (such as submitting forms), use POST methods instead of GET. This helps prevent unwanted actions through forged requests.
Protection Against Logging and Credential Theft
- Check Your Email for Password Leaks: Use the service Have I Been Pwned to check if your password has been leaked on any websites. If it has, your site may also be at risk, as many people use the same password across multiple services. It’s crucial to break this bad habit.
- Use Strong Passwords: Require users to create complex and unique passwords. Encourage the use of special characters, numbers, and a combination of uppercase and lowercase letters.
- Implement Two-Factor Authentication (2FA): Enable 2FA to add an extra layer of security for user accounts.
- Regularly Update Passwords: Change your passwords at least every six months. Ensure that you don’t simply modify an existing password slightly, as this can still be easily guessed.
- Monitor and Log Activities: Set up login and user activity logging with plugins like WP Activity Log. This allows you to track suspicious activity and respond promptly to potential threats.
- Educate Users: Train users, especially administrators, about the importance of credential security and how to recognize phishing attacks and other threats.
- Use Password Management Services: For secure storage and quick access to your accounts, consider using specialized services like Bitwarden.
Vulnerabilities in Plugins and Themes
- Regular Updates: Regularly update all components of your site, including WordPress, plugins, and themes, to eliminate vulnerabilities.
- Use Security Plugins: Employ security plugins such as Wordfence, iThemes Security, or Shield Security for additional protection.
- Code Analysis for Custom Plugins and Themes: If you are developing your plugin or making changes to a theme’s code, always run it through a code analyzer like WPCS (WordPress Coding Standards). If you’re not familiar with it, read an article about it here.
Uploading Malicious Files
- Restrict File Types for Upload: Ensure that you only allow specific file types to be uploaded.
- File Type Settings: You can configure this in WordPress using functions such as wp_handle_upload_prefilter() and wp_check_filetype() to enforce file type restrictions.
- Use Security Plugins: Employ security plugins to enhance protection against malicious file uploads.
- Automated Malware Scanning: Set up automatic scanning of uploaded files for malware using antivirus software or scanners like ClamAV.
- Limit File Access Permissions: Ensure that file and directory permissions are set correctly. For example, set permissions to 755 for directories and 644 for files to restrict write access.
XML-RPC Attacks
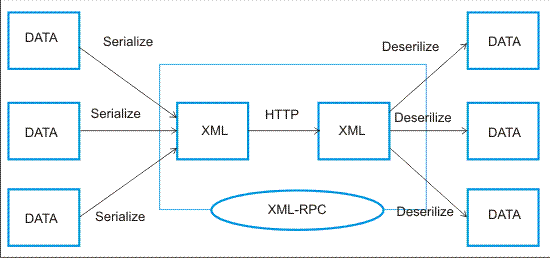
- Disable XML-RPC: You can use Wordfence to help disable XML-RPC functionality if it’s not needed.
- IP Address Access Restrictions: Limit access to the XML-RPC endpoint based on IP addresses.
- Request Rate Limiting: Implement limits on the number of requests made to the XML-RPC endpoint.
- Log Monitoring: Set up monitoring of your server logs to track suspicious activity and abnormal requests to xmlrpc.php.
- Use CAPTCHA or Similar Solutions: Implement CAPTCHA or similar solutions to verify that requests are made by humans.
Directory Traversal (Directory Path Attack)
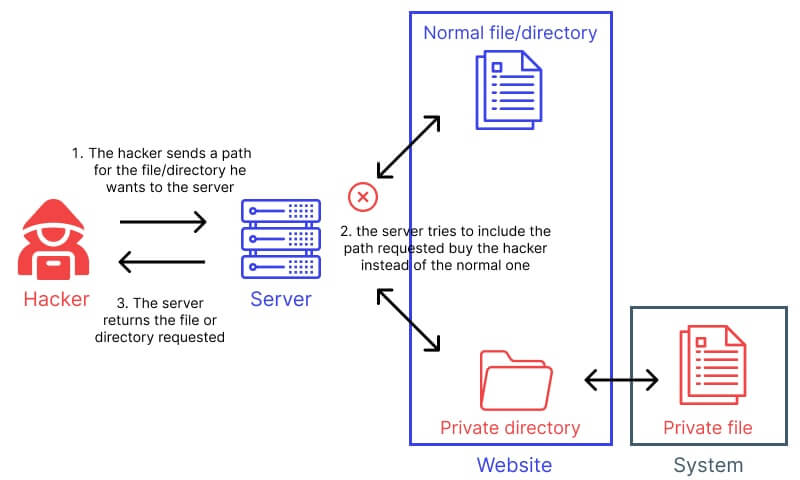
- Regularly Update WordPress, Plugins, and Themes: Developers often fix vulnerabilities that can be exploited for Directory Traversal attacks.
- Ensure Correct File System Permissions: Set permissions to 755 for directories and 644 for files to limit unauthorized access.
- Restrict Access to Confidential Files: Limit access to sensitive files to prevent unauthorized retrieval.
- User Input Validation: Implement validation of user input not only on the front end but also on the back end.
- Use WordPress API Functions: Utilize WordPress API functions for working with files and directories. For example, functions like ABSPATH and plugin_dir_path() help handle files securely and avoid access issues.
- Use SFTP Instead of FTP When Possible: Ensure secure access to the file system by using SFTP, and make sure FTP access is restricted and secured.
- Set Up a Web Application Firewall (WAF): Configure a WAF to filter suspicious requests and block potential server-level attacks.
Remote File Inclusion (RFI) and Local File Inclusion (LFI)
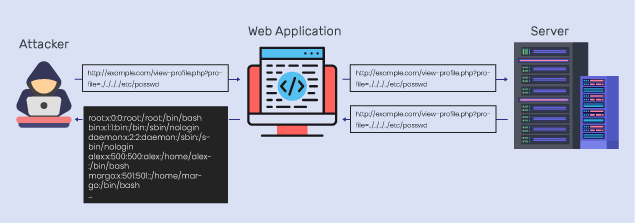
- Regular Updates: Keep WordPress, plugins, and themes up to date to patch vulnerabilities that could be exploited.
- Use Built-in WordPress API Functions: Utilize functions such as plugin_dir_path() and get_template_directory() for working with files, which help avoid using insecure paths.
- Always Validate and Filter User Input: Especially if user input is used to determine file paths. Use regular expressions to check for valid values and prevent the use of special characters.
- Restrict File Types: Limit the types of files that can be uploaded or included on your site.
- Set Up Proper File and Directory Permissions on the Server: Ensure the correct permissions are in place to avoid unauthorized access.
- Disable allow_url_fopen in PHP Settings: If possible, turn off this function to prevent remote file inclusion via URL.
- Never Use Relative Paths for File Inclusion: Always use absolute paths and environment variables such as ABSPATH to ensure you are only accessing authorized files.
- Protect Sensitive Files from Direct Access: Make sure confidential files (e.g., wp-config.php) are not directly accessible via the web server by using server configurations or an .htaccess file.
- Filter Special Characters in File Inclusion Functions: Make sure functions that include files prevent the use of paths that could lead to unauthorized file access.
Phishing Through Compromised Websites
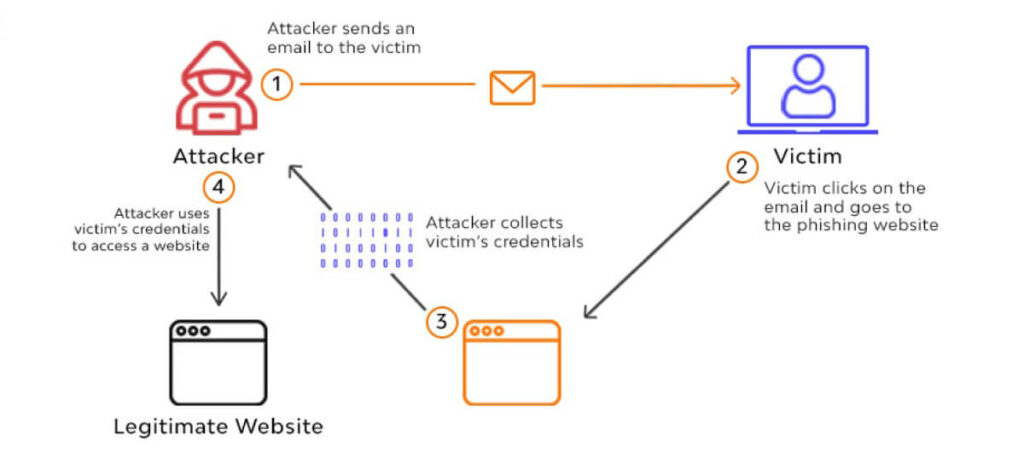
- Regularly Check Your Site’s Content: Monitor for suspicious links or materials that could indicate phishing activity.
- Configure a Web Application Firewall (WAF): Use a WAF to filter out suspicious requests and prevent unauthorized access.
- Regularly Backup Your Website: This ensures you can restore your site in case of a compromise or data corruption.
- Install Security Monitoring Plugins: Use tools like Wordfence or Sucuri to track suspicious activity and hacking attempts.
- Use Strong and Unique Passwords for All Accounts: It is advisable to generate secure passwords using password generators.
Backdoor Attacks
- Keep WordPress, Plugins, and Themes Updated: Regular updates can patch security vulnerabilities that attackers may exploit.
- Regular Backups: Make frequent backups of your website, allowing for restoration if a backdoor is found.
- Set Proper File and Directory Permissions: Minimize the possibility of unauthorized file modifications by setting directories to 755 and files to 644.
- Malware Scanning: Regularly scan your site for malware using security plugins like Wordfence or Sucuri.
- Restrict Access to wp-admin and wp-login.php: Use plugins or web server settings to allow access only from specific IP addresses.
- Remove Unused or Unsupported Plugins and Themes: This eliminates potential vulnerabilities or hidden backdoors.
- Set Up File Integrity Monitoring: Monitor changes to critical files and receive alerts for suspicious activity.
Supply Chain Attacks
- Install Reputable Plugins and Themes: Choose plugins and themes with a good reputation, high ratings, and active support from developers. Review user feedback before installation.
- Secure Development Practices: If developing custom plugins or themes, use open-source repositories and regularly check dependencies for vulnerabilities.
- Monitor Activities: Use tools like WP Activity Log to track changes and detect suspicious behavior.
- Use Trusted CDN Sources: When using external libraries via CDN, choose well-known and reliable sources like Google.
- Limit External Requests: Minimize the number of external requests your site makes, particularly if they could result in remote code execution.
Clickjacking Protection
- Security Headers Check: Regularly inspect your site’s security headers with tools like Security Headers to ensure your settings meet current security standards.
- Security Plugins: Use security plugins (e.g., Wordfence, Sucuri) to monitor suspicious activity and potential attack attempts.
- Limit JavaScript Usage: Avoid using unnecessary or third-party JavaScript that can introduce vulnerabilities.
- Keep WordPress Updated: Regularly update WordPress, plugins, and themes to address any known vulnerabilities.
- Content Security Policy (CSP): Configure CSP headers to restrict where resources can be loaded from, preventing malicious content from being framed on your site
- Use X-Frame-Options Header: Set the X-Frame-Options header to DENY or SAMEORIGIN to block your site from being embedded in iframes by attackers.
We have described all the possible vulnerabilities your website may face. I hope this article will be useful to you, and your site will remain fully secure. I would also like to add that most of these vulnerabilities can be automatically mitigated, even on the free plan, with the Wordfence plugin or its competitors. By taking care of your website’s security, you ensure its reliable operation and the protection of your users’ data.
Conclusion
In today’s digital world, securing WordPress websites has become a critically important task. Various attacks, such as Clickjacking, Backdoor, Supply Chain, and many others, can cause significant harm to both users and site owners. However, by taking proactive measures such as regular updates, using security headers, validating user data, and monitoring activity, the risk of site compromise can be significantly reduced.
Educating users about potential threats and providing information on safe online behavior also play a key role in creating a secure online environment. It is important to remember that security is not a one-time task but an ongoing process that requires attention and regular updates to practices. By implementing the listed measures, you can create a safer environment for your WordPress site and protect both your data and your users’ data.
Related posts
Insights and Tips from My Journey

- Category:
- Maintenance
Setting Up GitHub Actions for Automatic WPCS Verification: A Guide for PHP and WordPress
Ready to Take Your Project
to the Next Level?
Let’s bring your vision to life with expert development and custom solutions.
Contact us now and get started on transforming your ideas into reality!

